Developers Guide to inject Conjur Secrets using Summon - V 1
Getting Started
- CyberArk Safes will be automatically created during workspace provisioning. Login in to https://pvwa.corp.netapp.com/PasswordVault/v10/Accounts and retrieve the username and password of your Dev/Stg/Prod Safe from the API Safes - > eg:
S-D-C-RNCHR-CNJR-< appcode >-api. Refer the below image.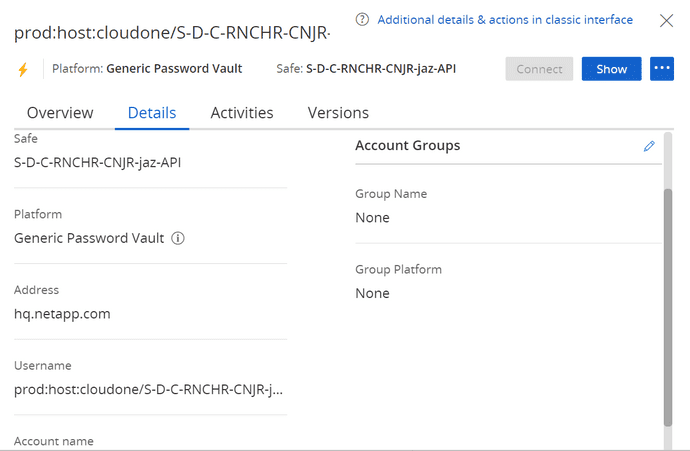
- Summon CLI Installation - Summon provides an interface for fetching secrets from a variety of trusted stores and exporting the secret values as environment variables to a sub-process environment. To setup summon download and install Summon cli and Summon-Conjur Provider. See the Summon GitHub repo for installation instructions. Download Summon CLI - https://github.com/cyberark/summon/releases Download Summon Conjur Provider - https://github.com/cyberark/summon-conjur/releases.
Note Windows Users should download .exe executable and linux users -amdx64 for both summon and summon-conjur
Local Workspace Preparation
- Place the summon.exe and summon-conjur.exe executables in the same folder. Preferably in your application source directory so as to execute it from there.
- Create a conjur.conf and place it in the same directory as the executables.
- Download Conjur certificate in .pem format (Download from the Conjur Application Safe -CORP SAFE S-P-C-VLT-CONJUR-CERT).
- Add the following content to the conjur.conf file:
---
account: prod
plugins: []
appliance_url: https://follower-west.corp.netapp.com
cert_file: <path to the conjur-conjur.pem file>"cert_file should be the absolute path of the pem file
- Create secrets.yml in the same directory as the executables.
- Add the following content to the secrets.yml file:
Name of the secret variable to be used in the application codebase>: !var secret variable to retrieve from pvwa.
Coin the secret variable like this - prodvault/CloudOne_LOB/<-SafeName->/<-accountname->/<-variablename->
Account Name is the unique name of the account that you create in CyberArk.
Variable Name is the username or password field of the CyberArk secret that should be retrieved.
Refer the below template.
SECRET: !var prodvault/CloudOne_LOB/S-D-C-RNCHR-CNJR-jaz/sample_db/password
- Open Command Terminal as Administrator and set the following environment variables.
This is the username and password retrieved from Step 1.
Note that the username should look like - host/cloudone/
windows:
set CONJURRC=<path_to_executables_directory>\conjur.conf
set CONJUR_AUTHN_LOGIN=<username> host/cloudone/<SafeName>-id1, SafeName depends on the lanscape.
set CONJUR_AUTHN_API_KEY=<api_key> This is the password to the hosted account in pvwa.linux:
export CONJURRC=<path_to_executables_directory>\conjur.conf
export CONJUR_AUTHN_LOGIN=<username> host/cloudone/<SafeName>-id1, SafeName depends on the lanscape.
export CONJUR_AUTHN_API_KEY=<api_key> This is the password to the hosted account in pvwa.Consume secrets in application.
- Run Command Prompt as Administrator in your application source directory.
- Run below command to test secret retrieval from Conjur:
For Windows users
summon.exe -p .\summon-conjur.exe powershell.exe -c "Write-Output $env:SECRET" For Linux Users
./summon-linux_amd64 -p ./summon_conjur_linux_amd64 bash -c 'echo $SECRET' If you get network unaccesible issue please nslookup follower-west.corp.netapp.com and make sure it is reachable from your terminal.
This retrieves the secret from conjur and prints the same in powershell.
- To run a springboot application and inject secrets to it use the below command.
summon.exe -p .\summon-conjur.exe mvn:spring-boot:run. The secret is now injected as an environmental variable and is ready be used in Springboot as a system environment variable.